Exposed: Israeli-backed AI network weaponized X to foment chaos in Iran during 12-day war
By Maryam Qarehgozlou
A new investigation has exposed a coordinated Israeli-backed network of fake X accounts using AI-driven tactics to spread disinformation and—unsuccessfully—stir unrest and indoctrinate the Iranian public against their government.
The findings come from the University of Toronto’s Citizen Lab, a renowned digital research group specializing in uncovering spyware, surveillance, and state-sponsored deception.
According to Citizen Lab, the network—dubbed “PRISONBREAK”—was established in 2023 but gained significant momentum following the unprovoked and illegal Israeli military aggression against Iran in June, continuing its activities to the present day.
The research indicates that the campaign was not a freelance effort. Instead, it was coordinated directly by an Israeli regime agency through one of its closely supervised subcontractors.
Darren Linvill, co-director of the Watt Family Innovation Center Media Forensics Hub at Clemson University, first detected the initial traces of this disinformation drive.
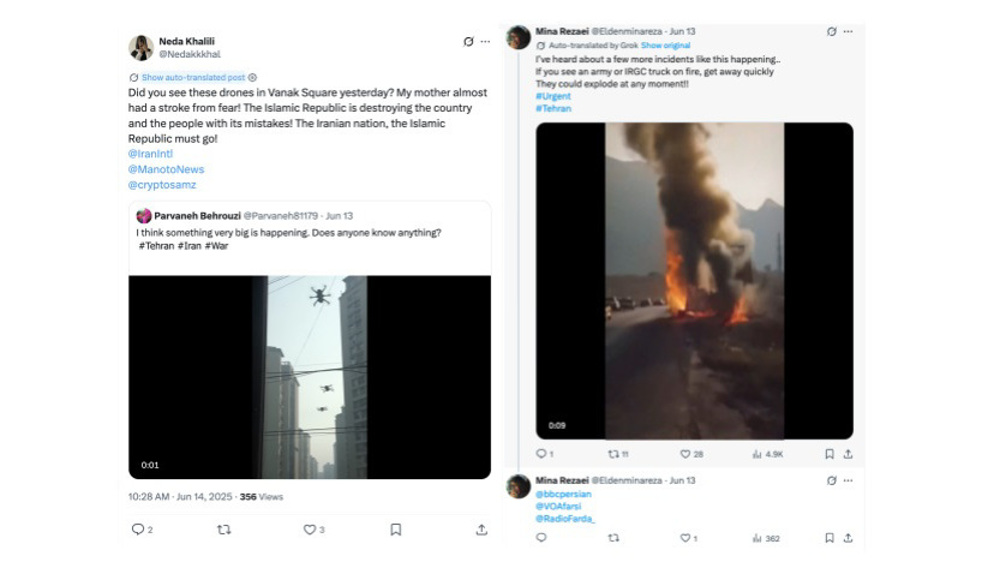
Linvill and his team identified 37 X accounts exhibiting synchronized behavior—posting at identical hours, using the same uncommon “Twitter Web App” client, and relying on stolen profile photos devoid of any personal details. Many accounts shared identical hashtags and content, pointing to centralized command.
All of these accounts were created in 2023 and, according to Linvill, they remained largely inactive until January 2025, suggesting they were sleepers awaiting activation.
Their coordinated posting during Israel’s twelve-day war on Iran—and the apparent pre-prepared AI-generated material—suggests foreknowledge of Israeli military strikes against the Islamic Republic, according to the research.
Evin Prison bombing and deepfake deception
The Citizen Lab report reveals that PRISONBREAK was first exposed through interactions surrounding an AI-generated video falsely depicting the bombing of Tehran’s high-security Evin Prison, a fabrication the researchers called “a highly sophisticated deception attempt.”
On June 23, Israeli forces carried out a devastating series of strikes against Evin Prison between 11:17 a.m. and 12:18 p.m., marking the deadliest day of Israel’s unprovoked war on Iran.
The missiles struck multiple areas—including the library, clinic, prosecutor’s office, meeting rooms, and cell blocks—causing massive destruction during visiting hours.
One of the missiles hit the entrance to the prison, where prisoners often wait to be transferred to the hospital or court.
The attack left over 100 people dead, including prisoners’ family members, social workers, lawyers, doctors, nurses, a five-year-old child, several conscripted soldiers, administrative staff, and residents of the area.
Citizen Lab identified that the first PRISONBREAK-linked post about the explosion appeared at 11:52 a.m. Tehran time, just minutes after the bombardment began.
A confirmed PRISONBREAK account – @kavehhhame – was the first to post about it.
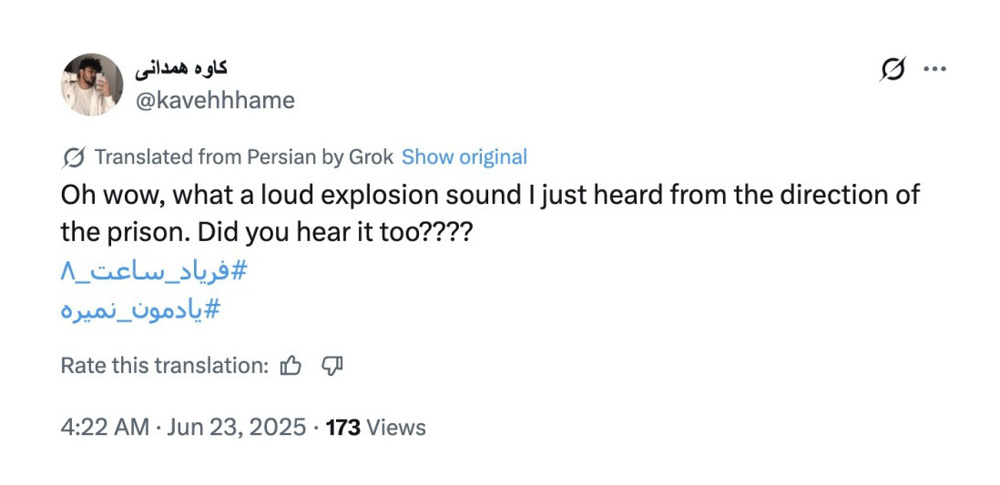
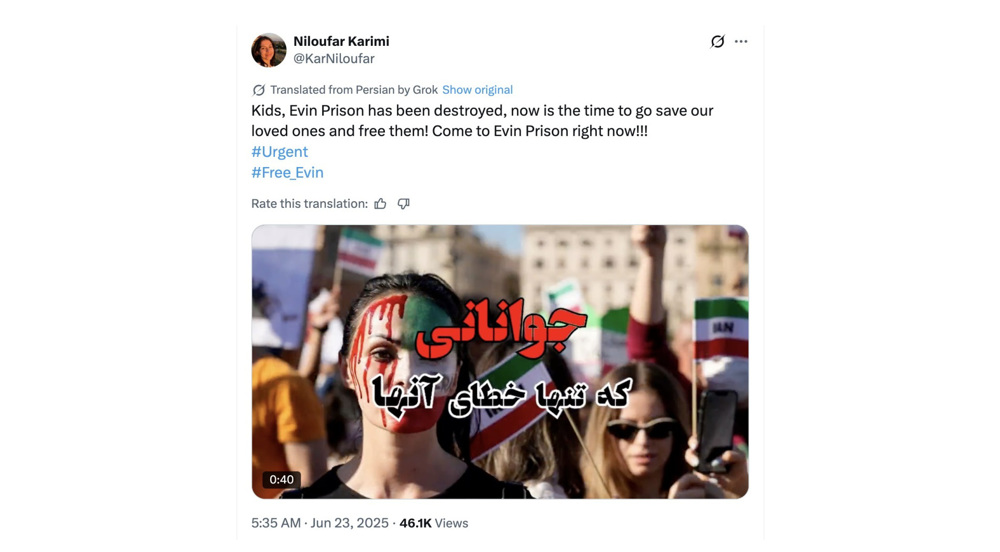
Another account, @KarNiloufar—the oldest in the network—shared a deepfake video of the strike on the prison entrance at 12:05 p.m., while the attacks were still underway.
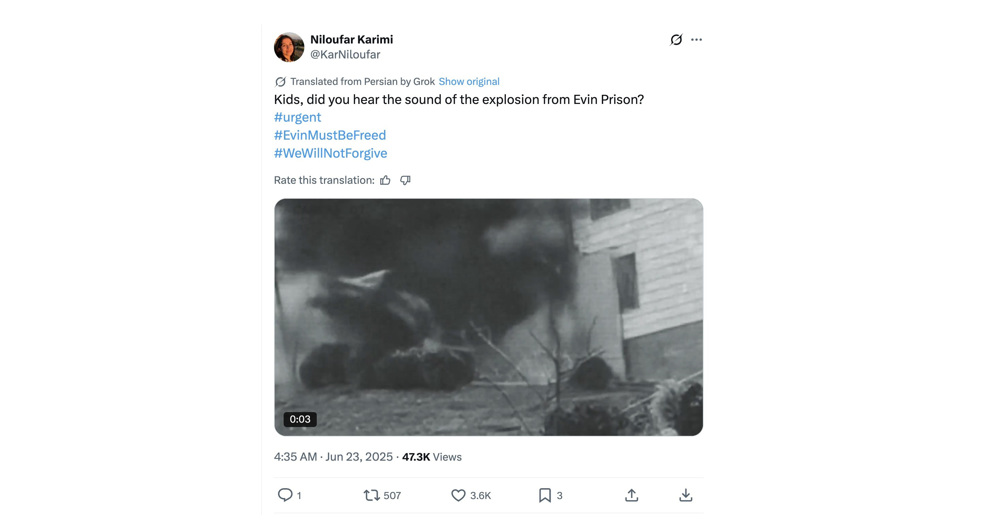
The fabricated footage was widely circulated and even amplified by international outlets.
“The exact timing of the video’s posting, while the bombing on Evin Prison was allegedly still happening, points towards the conclusion that it was part of a premeditated and well-synchronized influence operation,” says Citizen Lab.
In the minutes following the video’s release, other PRISONBREAK accounts added their own contributions, claiming to have heard the sound of the explosions hitting Evin.
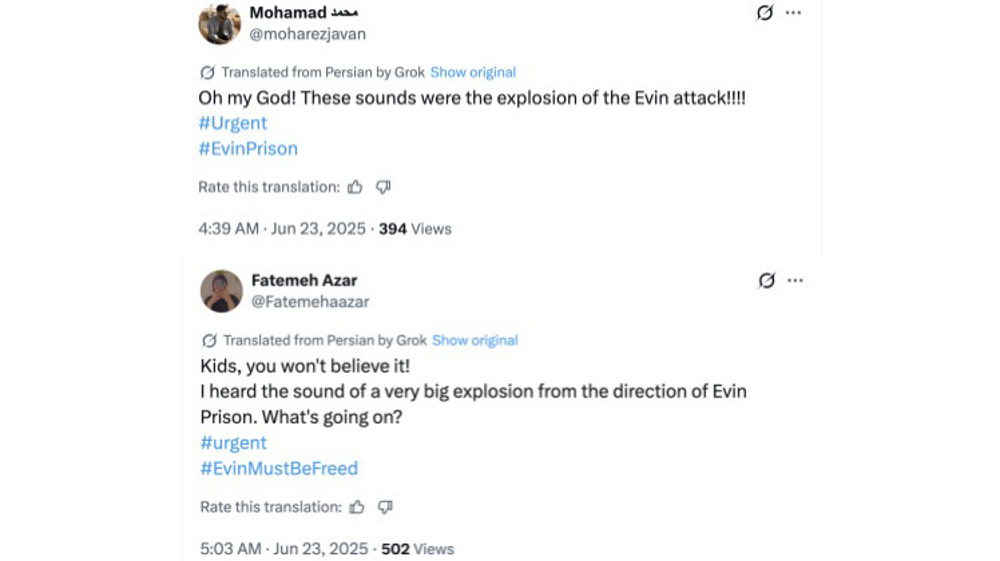
After the bombings reportedly ended at 12:36 p.m. Tehran time, the network started explicitly calling for the capital city’s population to reach Evin and free the prisoners.
The X accounts also posted reassuring statements such as “the attack will end now” and “the area is safe.”
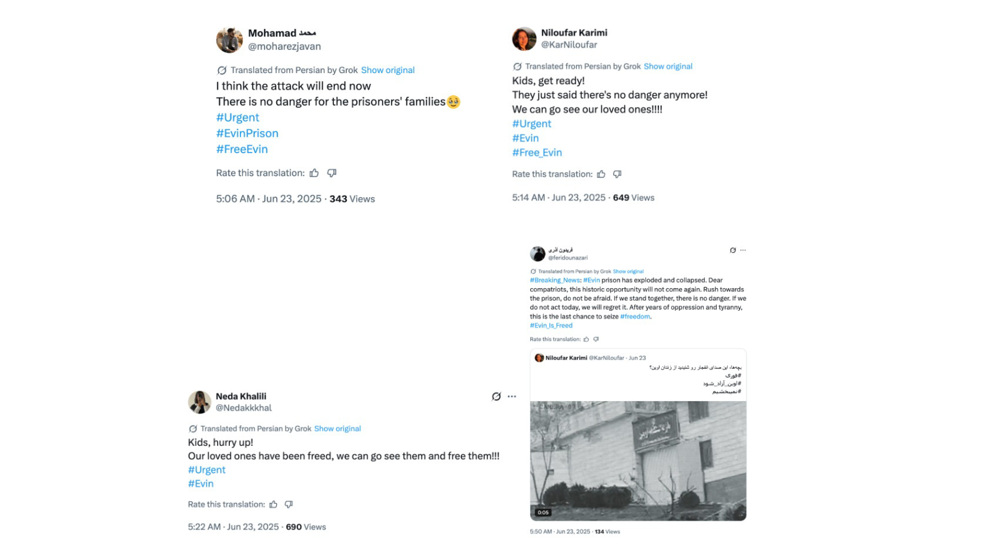
Within almost an hour of posting the AI-generated video purportedly showing the bombing of the main entrance of Evin Prison, the original video sharer, @KarNiloufar, shared another post, which also included a video.
While the posts by the PRISONBREAK network’s accounts calling for people to reach the prison achieved virtually no organic engagement and a very low amount of views, @KarNiloufar post amassed 46,000 views and over 3,500 likes.
The PRISONBREAK network reshared the post several times.
“This second video about the Evin Prison, which shows the hallmarks of professional editing and was posted within one hour of the end of the bombings, further strongly suggests that the PRISONBREAK network’s operators had prior knowledge of the Israeli military action, and were prepared to coordinate with it,” Citizen Lab said.
Engineering chaos: Calls for "regime change"
The Evin Prison deepfake was only one piece of PRISONBREAK’s larger anti-Iran narrative.
Citizen Lab’s analysis shows the network’s ultimate goal was to foment so-called "regime change" by fabricating images of unrest, instability, and public anger inside Iran during the war.
“Upon further analysis of the PRISONBREAK network’s posting timeline and post content, we assess that their primary narrative was one of regime change in Iran,” the research lab said.
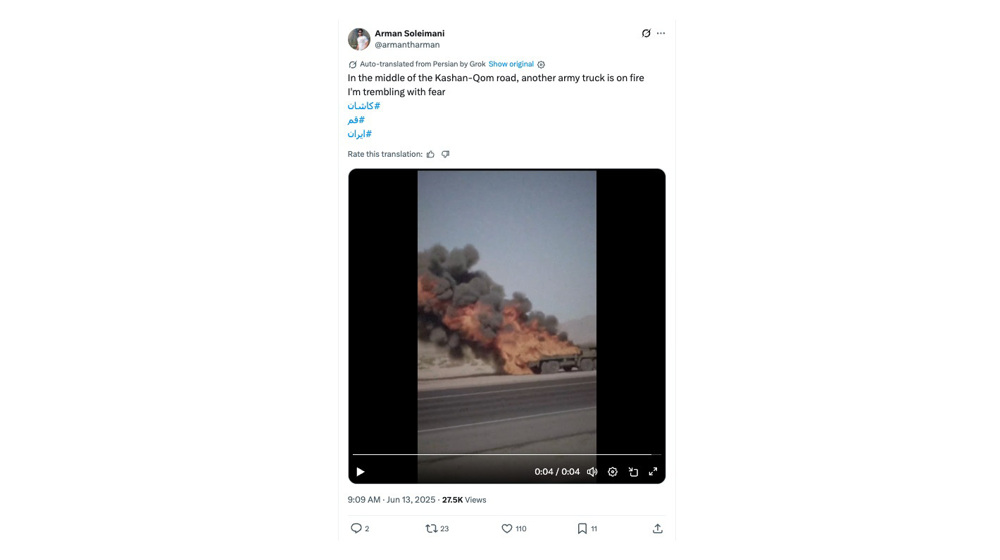
From the very first day of the Israeli assault on June 13, the network began spreading videos claiming to show explosions of Iranian military vehicles and protests breaking out nationwide.
At least nine such posts appeared that day—many likely AI-generated composites—designed to create an illusion of chaos, Citizen Lab said.
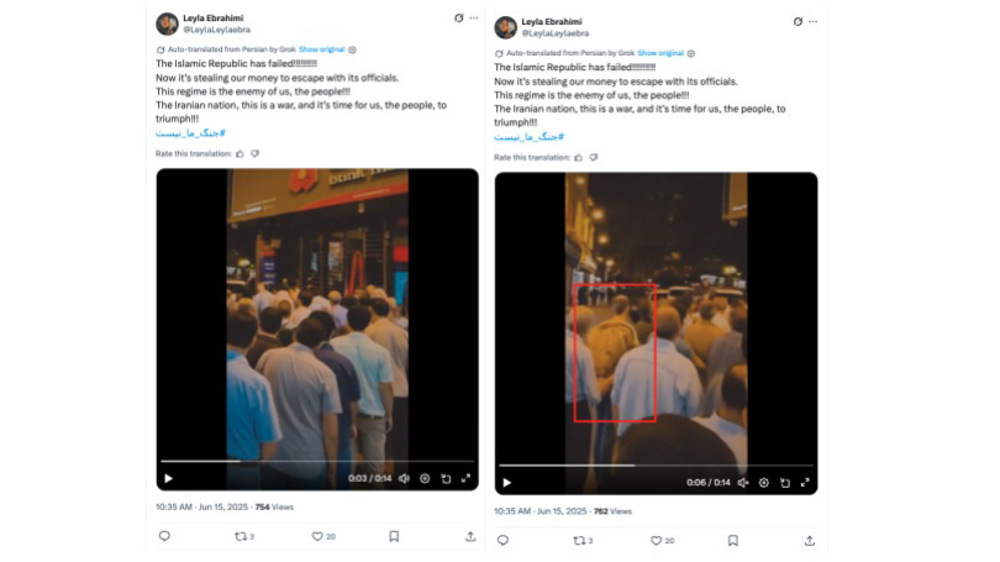
Two days later, as Israel’s bombings continued, PRISONBREAK accounts began circulating messages alleging economic collapse, urging citizens to head to ATMs to withdraw money, claiming that the Islamic Republic was “stealing our money to escape with its officials,” urging followers to rise up.
“At least two of the observed posts, which depict long lines of people waiting at the bank and beginning to riot, show elements of AI generation,” the report said.
In the posts shared in the investigation, one of the bodies blurs and becomes misshapen, suggesting the footage was AI-generated, it added.
Between June 20 and 22, the network attempted to spark synchronized protest actions through the hashtag “8 o’clock cry”, calling on Iranians to chant anti-government slogans from their balconies at 8 p.m. nightly.
Citizen Lab documented at least nine videos and 23 posts promoting the campaign between June 20 and 22, although most of the videos lacked visible participants and appeared to be manipulated.
“[…] we are able to conclude that at least some of the videos were manipulated. As we could not identify them as posted anywhere else, we conclude that the videos were likely created by the account operators,” the report said.
Despite the extensive resources invested in Israel’s digital interference effort, the PRISONBREAK operation failed to achieve traction inside Iran. The attempts to incite riots, spark a prison uprising, or engineer public panic fell flat.
However, it did not stop its dissemination of content promoting an uprising against the establishment.
Even after June 24, when Israel was forced into a ceasefire following devastating retaliatory Iranian strikes, the network continued to push anti-government content—this time questioning the ceasefire and spreading rumors that employees had not been paid.
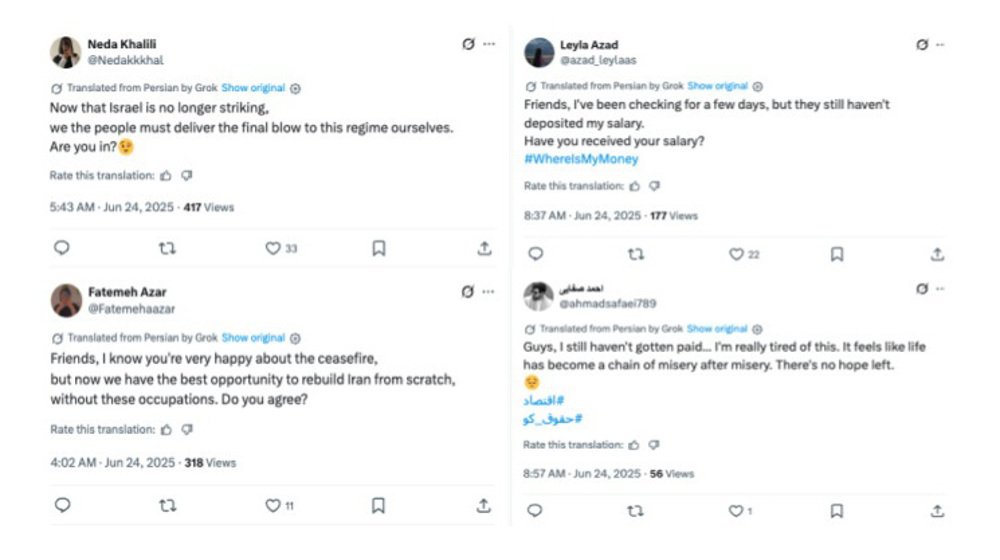
Manufactured legitimacy
Beyond its AI-generated fabrications, the PRISONBREAK operation also engaged in media impersonation, posing as national and international news outlets to lend credibility to its propaganda.
According to Citizen Lab, one of the most striking examples involved BBC Persian, which was impersonated through a fake article screenshot and two fabricated videos.
The post, shared by the account @KarNiloufar, claimed that BBC Persian had deleted the article within five minutes of posting it. The falsified headline read: “Officials flee the country; High-ranking officials leave Iran one after another.”
However, Citizen Lab confirmed directly with BBC Persian that no such article was ever published by the broadcaster.
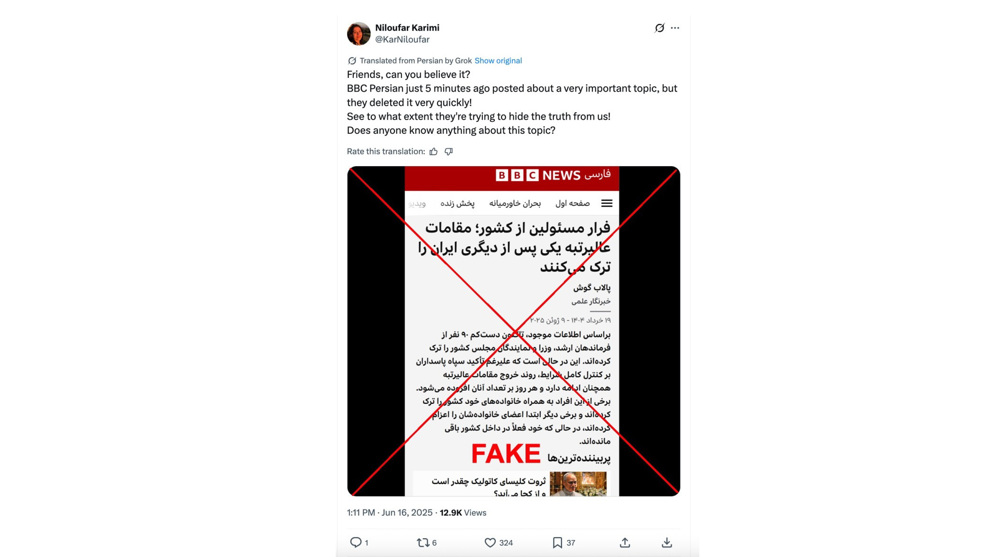
Days later, the network circulated two additional videos disguised as BBC Persian reports.
The first purported to summarize the 12-day US-backed Israeli war on Iran, emphasizing alleged “heavy traffic, gas shortages,” and suggesting that Iranian officials had abandoned the government.
The second carried the fabricated title “Special daily summary of the attack on the regime’s repressive forces” and included the network’s earlier Evin Prison deepfake along with clips of other supposed explosions across Iran.
Once again, BBC Persian confirmed to Citizen Lab that it neither produced nor aired this content.
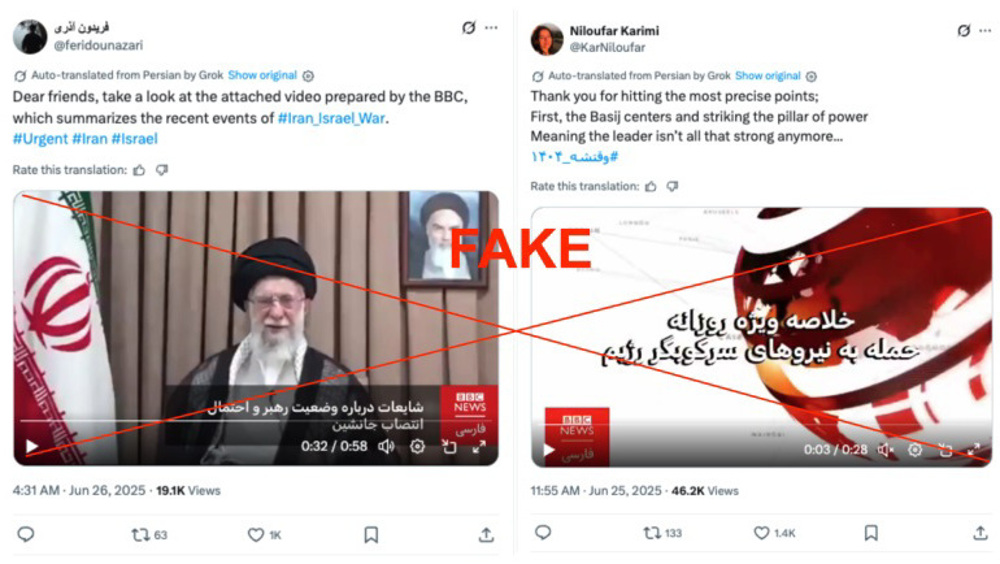
Citizen Lab also identified further examples of media impersonation, this time targeting Afkar News. The accounts shared screenshots of headlines with links claiming to lead to Afkar News articles.
“In both instances, the links do not lead to a news article, nor were we able to locate archived versions,” the report noted, pointing to deliberate deception.
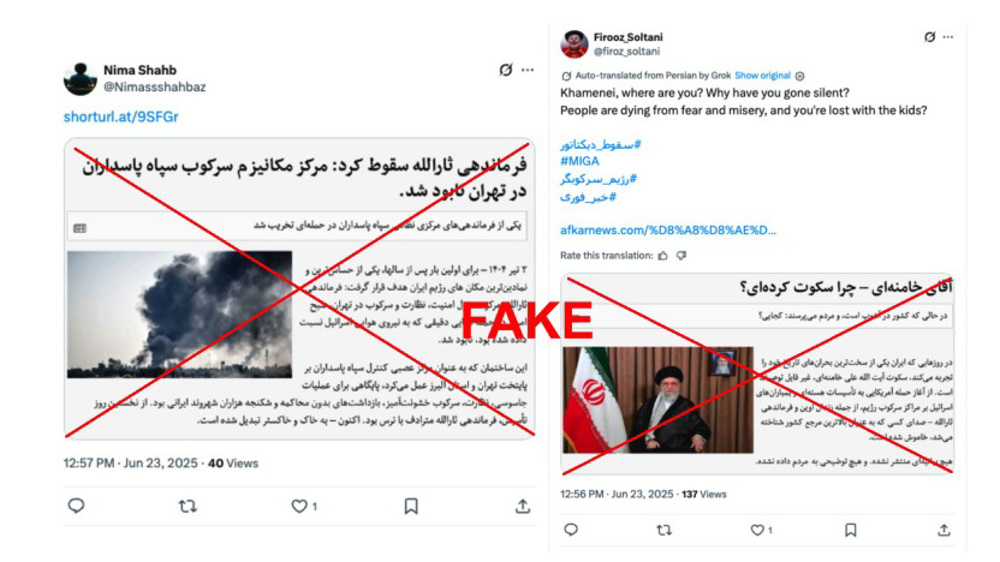
Recycled footage
Citizen Lab found that the operation frequently recycled or manipulated existing videos to mislead viewers about "protests" or "unrest" in Iran.
In three cases, the network’s accounts claimed to have filmed the scenes themselves, but the lab confirmed the footage had been taken from unrelated sources days earlier.
Some clips had been cropped and re-edited to conceal their origins. The researchers observed that many videos were also looped and overlaid with dubbed or mismatched audio.
“The lack of continuity suggests that the audio has been added overtop of the video, pointing to its manipulation,” the report stated.
Artificial amplification
While PRISONBREAK’s content achieved low genuine engagement, the operators attempted to artificially boost their visibility.
To inflate reach, they targeted anti-Iran online communities and posted within Persian-language “Follow Back” groups, which promise mutual follows to rapidly expand user bases, according to the report.
“By using X Communities to spread their content, PRISONBREAK artificially inflated the viewership on several posts, increasing their chances of influencing their target audience through the community members’ resharing,” it noted.
In addition to infiltrating such communities, the accounts also constantly reshared each other’s posts, especially those suspected of being AI-generated.
Citizen Lab described this as a form of self-amplification—a way to simulate popularity and legitimacy.
“This technique can be observed on nearly all of the network’s accounts, in an attempt to spread their content to as many users as possible and increase the effectiveness of their covert influence campaign,” it said.
In a further attempt to attract mainstream attention, PRISONBREAK accounts frequently tagged Western-funded Persian-language media outlets hostile to Iran—such as BBC Persian, VOA Farsi, and Iran International—platforms that have long been echoing Israeli psychological warfare narratives.
“Given the success of the Evin Prison deepfake in tricking mainstream media, tagging news accounts on other videos allegedly produced by the network demonstrates a persistent attempt to deceive the media with inauthentic twelve-day war content in line with the network’s narratives,” Citizen Lab stated.
Fabricated personas
Citizen Lab’s analysis concludes with “high confidence” that the PRISONBREAK network is both “coordinated” and “inauthentic.”
“It does not represent existing individuals, and was almost certainly orchestrated by a professional team, following a specific playbook,” the researchers wrote.
One telling clue was the network’s use of a nonstandard email domain—@b********.***—for registering about half of its X accounts.
“We note that it does not appear to be one of the most commonly used webmail services – i.e. Gmail, Outlook, Hotmail, or Office – and the character count does not match other popular services starting with “b”, such as, for example, btinternet.com,” the report said.
Citizen Lab concluded that the obscure or proprietary nature of the domain strongly indicates tight coordination among the operators.
Although all accounts were created in 2023, 99.5 percent of their activity occurred only after January 2025, further confirming their coordination and inauthenticity, the research lab said.
The report also found that the network’s posting schedules mirrored a structured workday, suggesting the presence of a professional disinformation team rather than random users.
Additionally, PRISONBREAK relied heavily on X’s desktop application—a tool preferred by professional operators—rather than mobile apps commonly used by ordinary users.
Profile photos across the network were also suspiciously faceless, sourced from stock image databases, or lifted from platforms like Pinterest, another hallmark of fabricated personas.

Tracing the source
While Citizen Lab refrains from definitive attribution, its evidence overwhelmingly points to Israeli involvement.
The researchers conclude that the most probable scenario is that of an involvement by the Israeli regime, either an agency working alone or with the participation of an outside contractor.
Two alternative possibilities were considered: involvement by the US government or a third-party state, though these were deemed less likely.
“We judge these two hypotheses as having medium-high and low likelihood, respectively,” it concluded.
The PRISONBREAK network is not an isolated case.
In a related revelation, the Israeli daily Haaretz disclosed that Israel recently ran another covert campaign, this time using fake accounts and AI-generated content to promote Reza Pahlavi, the son of Iran’s deposed Shah.
The operation aimed to revive monarchist sentiment and push for the restoration of the monarchy—further evidence of Israel’s continuous interference in Iran’s domestic affairs under the guise of social media activism.
Furthermore, over the years, both independent media investigations and social media platform audits have uncovered a long trail of covert Israeli digital operations—each reflecting a pattern of manipulation, disinformation, and psychological warfare closely tied to the regime.
Two of the most prominent examples are Team Jorge and the Archimedes Group—Israeli-based influence-for-hire firms that weaponized digital tools to sway political outcomes worldwide.
Both entities boasted connections to Israel’s intelligence community, using advanced technology to construct elaborate propaganda ecosystems and offer their services to paying clients around the globe.
Team Jorge is the codename for a shadowy network of Israeli contractors specializing in cyber sabotage, hacking, and social media disinformation campaigns to manipulate the outcomes of elections.
The group’s operations were exposed in February 2023 following an undercover investigation led by Israeli and French journalists.
According to an exposé, the organization had been active since at least 2015 and claimed responsibility for manipulating 33 presidential elections across the world—27 of which it boasted were successful.
Most of these operations targeted African nations, though the group’s reach extended far beyond the continent, highlighting the global scale of Israel-linked interference networks.
Another case is the Archimedes Group, a Tel Aviv-based private intelligence and influence firm that has operated since 2017, running political manipulation campaigns through social media platforms.
In 2019, Facebook permanently banned the company for engaging in “coordinated inauthentic behavior” after uncovering its network of fake users operating across sub-Saharan Africa, Latin America, and Southeast Asia.
Facebook’s investigation revealed that Archimedes had spent approximately $1.1 million on deceptive advertisements—money funneled into fake political influence operations designed to distort public perception and democratic discourse.
AI-driven campaign promoted subversion during Israeli-American war on Iran: Research
— Press TV 🔻 (@PressTV) October 4, 2025
Follow Press TV on Telegram: https://t.co/LWoNSpkJSh pic.twitter.com/Ix91JJwOWa
‘Social media is a weapon’
Israel’s reliance on digital manipulation is no longer even covert. Benjamin Netanyahu recently admitted that his regime views social media as a weapon—a strategic tool to repair Israel’s collapsing image abroad amid mounting outrage over the ongoing genocide in Gaza.
To combat the flood of authentic footage and testimonies exposing Israel’s atrocities, especially in Gaza, Netanyahu urged the mobilization of sympathetic online figures.
“We have to fight back. How do we fight back? Our influencers. I think you should also talk to them if you have a chance, to that community, they are very important,” he said during a meeting in New York with American influencers aligned with Zionist causes.
The meeting was aimed at harnessing pro-Israel social media power to counter growing international condemnation.
Buying influence
Evidence of Israel’s orchestrated influencer campaigns soon emerged.
Bridges Partners, a firm contracted by the Israeli Ministry of Foreign Affairs, was revealed to have sent a series of invoices to Havas Media Group Germany, an international advertising agency working on behalf of Israel.
The invoices, covering a campaign period from June to November, outlined payments totaling $900,000 to finance an “Influencer Campaign” involving 14 to 18 online personalities.
The content plan called for 75 to 90 posts across major platforms such as TikTok and Instagram—effectively paying between $6,143 and $7,372 per post to promote pro-Israel narratives under the guise of independent commentary.
During the same meeting in New York with American influencers, Netanyahu also openly celebrated US government efforts to force TikTok’s sale to an American-controlled consortium, describing it as “the most important purchase going on right now, … number one.”
The proposed consortium—comprising Oracle, Michael Dell, and Rupert Murdoch—features long-standing allies of Israel.
The Israeli regime leader also emphasized the need to engage Elon Musk, the owner of X (formerly Twitter), possibly in an attempt to expand Israeli influence over online discourse and curtail the limited space still available for pro-Palestinian voices on the platform.
Activists caution that Israel’s information warfare reaches far beyond the occupied territories, weaponizing digital platforms to launder its image, manipulate global perception, and destabilize sovereign nations that resist its fascist settler-colonial agenda.
ElBaradei condemns US threats of military action against Iran
‘No two-hour war’: Iran vows immediate retaliation to any attack
VIDEO | US warmongering threatens stability
Pezeshkian: US must end provocations if it seeks genuine diplomacy
Iran summons German ambassador over Merz’s ‘low-minded’ remarks
Iran's Armed Forces warn EU of ‘consequences’ of IRGC designation
Iran FM: EU’s blacklisting of IRGC a ‘major strategic mistake’
EU blacklists IRGC in legally flawed move irrespective of consequences














 This makes it easy to access the Press TV website
This makes it easy to access the Press TV website